Top Takeaways from the 2023 Gartner® Hype Cycle™ for Security Operations
It’s official—the Gartner® 2023 Hype Cycle™ for Security Operations is here. As always, this year’s research reflects the changing dynamics of the threat landscape. Let’s delve into the technologies and practices revolutionizing security operations (SecOps), how they’ve evolved, and what security and risk leaders should consider as they build out their roadmap for 2024 and beyond.
Understanding the Hype Cycle
Gartner Hype Cycles provide a graphic representation of the maturity and adoption of technologies and applications, and how they are potentially relevant to solving real business problems and exploiting new opportunities. Over 90 Hype Cycles are published per year.
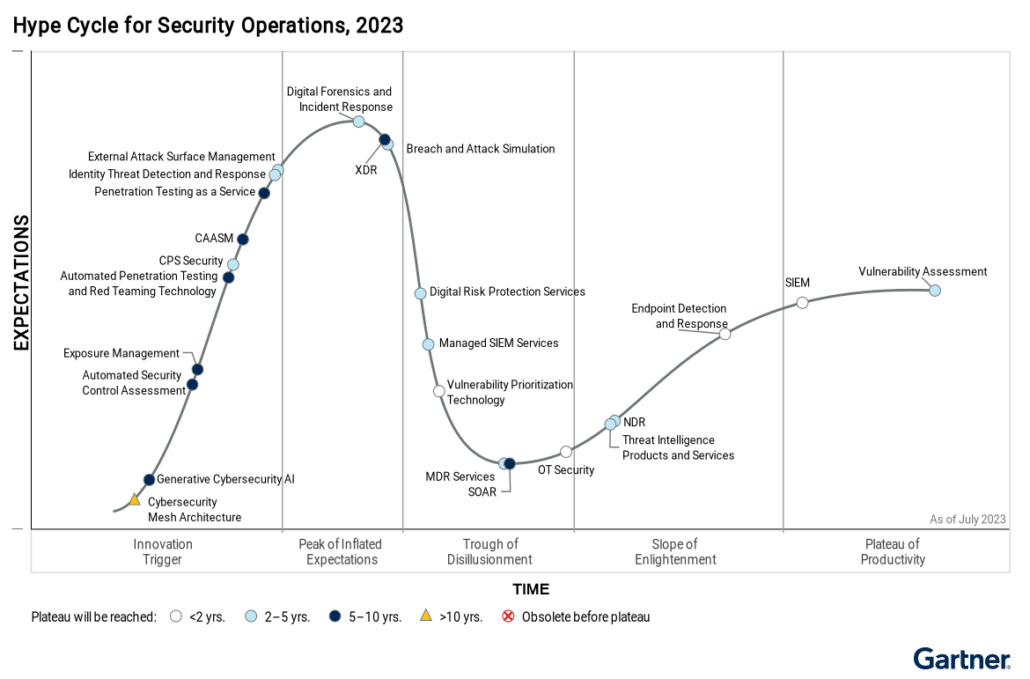
Each Hype Cycle drills down into the five key phases of a technology’s life cycle:
- Innovation Trigger
- Peak of Inflated Expectations
- Trough of Disillusionment
- Slope of Enlightenment
- Plateau of Productivity
Key Trends from the 2023 SecOps Hype Cycle
The 2023 Hype Cycle builds upon some of the foundations set forth last year, highlighting the maturation and evolution of technologies that help teams combat the growing complexities of today’s threat landscape. This concept is clearly emphasized by the categories that experienced the most significant rapid year-over changes, including:
- Cyber asset attack surface management (CAASM)
- Exposure management
- External attack surface management (EASM)
- Managed detection and response (MDR)
- Identity threat detection and response (ITDR)
- Extended detection and response (XDR)
In the ever-evolving cybersecurity landscape, staying ahead of the curve is not an advantage—it’s a necessity. As Chief Information Security Officers (CISOs) and other security and risk leaders build out their roadmap for 2024 and beyond, they should consider the following capabilities highlighted in this year’s Hype Cycle:
- Implement continuous threat exposure management (CTEM) concepts.
Exposure management has made it’s second appearance in this year’s Hype Cycle. Except this time, it’s advanced from “high” to “transformational” in terms of its benefits. Security and risk leaders face an increasing pressure to understand and manage the attack surface that is constantly growing and evolving. Exposure Management is a programmatic approach to resolving this, aligning different stakeholders to focus on broader cyber risk issues and drive prioritization.
- Improve the breadth and relevance of detection and response.
With the proliferation of connected devices and evolving attack vectors, it’s become paramount for security teams to enable fast, risk-driven prioritization and response decisions. Ten categories combine make up this year’s Innovation Trigger, each playing a role in organizations’ ability to continuously discover, assess, prioritize, validate, and/ or reduce threats and exposures.
- Maximize automation to reduce response times.
The attack surface continues to increase in complexity, requiring security and risk teams to adopt a dynamic, flywheel approach to the discovery and remediation of threats and exposures. Use cases for automation continue to grow and security leaders need to embrace them.
- Leverage generative cybersecurity AI for operational efficiency gains and skill augmentation.
Emerging in this year’s Hype Cycle, generative cybersecurity AI has the potential to improve existing workflows, cleanse analytics, and curate realistic attack data. While this method has the power to produce invaluable insights, big data analytics and data science techniques, can quickly lead to an ‘inundation of data’—causing more harm than good when implemented incorrectly.
Each of the 24 tools and services mentioned in the 2023 Hype Cycle for Security Operations offers its own insights, providing a unique layer of visibility. However, tool sprawl and data siloes can create real challenges for today’s defenders. According to Gartner:
“However, even with previous advancements made in data science and analytical interventions, these tools and services have led to an inundation of data, disparity in tooling, and ultimately end users managing the complexities of triage and analysis across a multitude of platforms. While many of these capabilities champion increased visibility, they also highlight the need for a more unified approach that is centered on better prioritization for faster, risk-based outcomes.
Noetic’s Take: Why SRM leaders should invest in CAASM?
Now in the latter phase of the Innovation Trigger stage, CAASM tools provide organizations with a comprehensive view of their entire attack surface so that they can make faster, more informed decisions that enable them to remain ahead of the adversary.
CAASM contributes to a more proactive security approach, allowing organizations to:
- Identify and Prioritize High-Risk Vulnerabilities: CAASM tools provide visibility and context into critical vulnerabilities on digital assets and their potential impact. This supports better vulnerability remediation and configuration adjustments to prevent exploitation.
- Streamline Compliance Efforts: Given the recent uptick in regulatory compliance requirements, such as the U.S.’s SEC cybersecurity regulations and the E.U.’s Network Information Security Directive (NIS2), security leaders must be able to present an accurate picture of their entire security posture to business leaders and regulators. CAASM assists organizations in aligning with industry standards and regulations by ensuring that their digital assets adhere to required security measures.
- Improve Incident Response (IR) Effectiveness: With a clearer understanding of their attack surface, security operations teams are able to triage suspected incidents based on their potential impact to the business, aligning exposure and business criticality in a way that was not possible before.
As Gartner® states in the report, a key benefit of CAASM is that it can “reduce dependencies on homegrown systems and manual collection processes and remediate gaps either manually or via automated workflows.“
Listed as a sample vendor in this year’s report, we see this across all Noetic customers.
They are able to reduce team workload by automating data collection, the delivering of exposure reporting and key metrics to different stakeholders, and simple remediation workflows, such as notifying the business owner of critical vulnerabilities or deploying missing endpoint agents.
Read more about the benefits of CAASM and updates on other key technologies for the modern Security Operations team in this year’s Gartner®: Hype Cycle for Security Operations.
GARTNER is a registered trademark and service mark of Gartner and Hype Cycle are a registered trademark of Gartner, Inc. and/or its affiliates in the U.S. and internationally and are used herein with permission. All rights reserved.
Gartner does not endorse any vendor, product or service depicted in its research publications, and does not advise technology users to select only those vendors with the highest ratings or other designation. Gartner research publications consist of the opinions of Gartner’s research organization and should not be construed as statements of fact. Gartner disclaims all warranties, expressed or implied, with respect to this research, including any warranties of merchantability or fitness for a particular purpose.
This graphic was published by Gartner, Inc. as part of a larger research document and should be evaluated in the context of the entire document. The Gartner document is available upon request from Noetic Cyber.
